Posted inVPN & Online Security
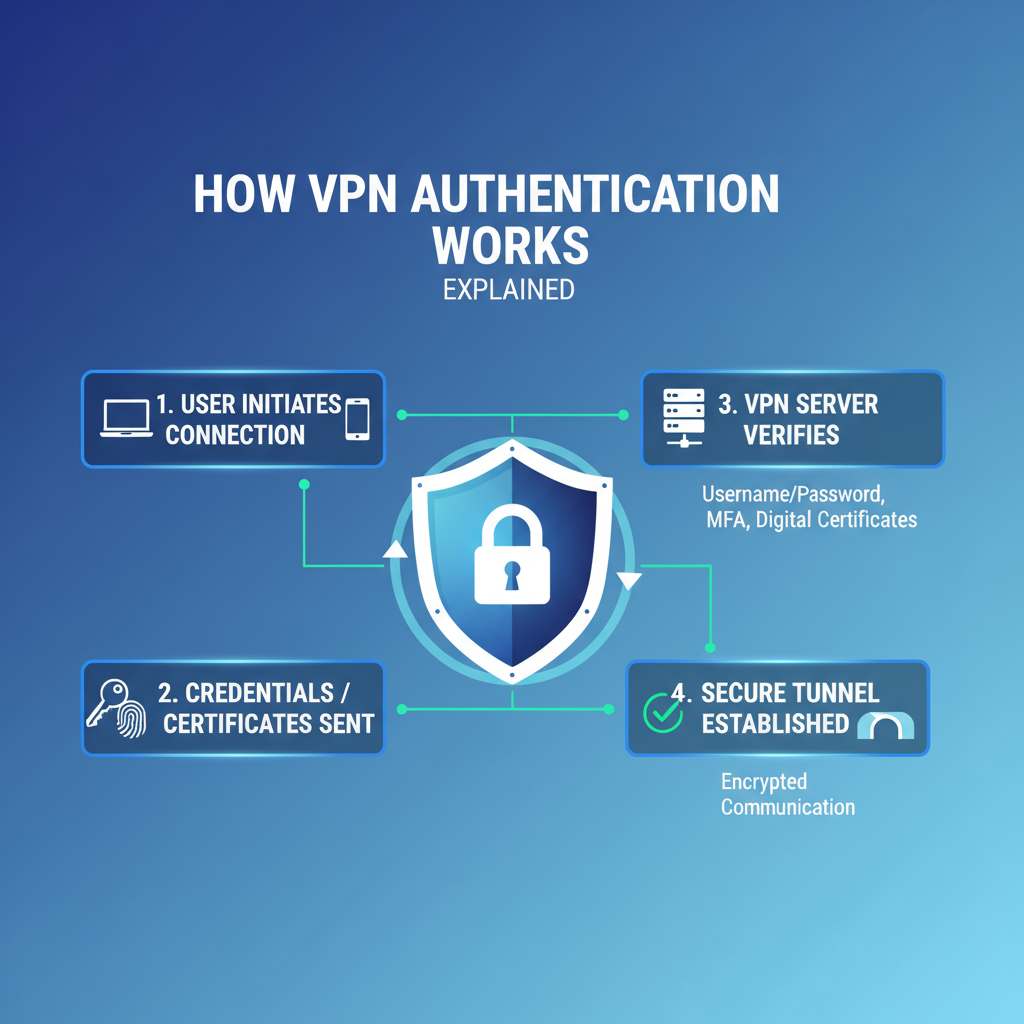
How VPN Authentication Works Explained
When using a Virtual Private Network (VPN), understanding how VPN authentication works is crucial for both security and privacy. VPN authentication is the process by which users confirm their identity before…