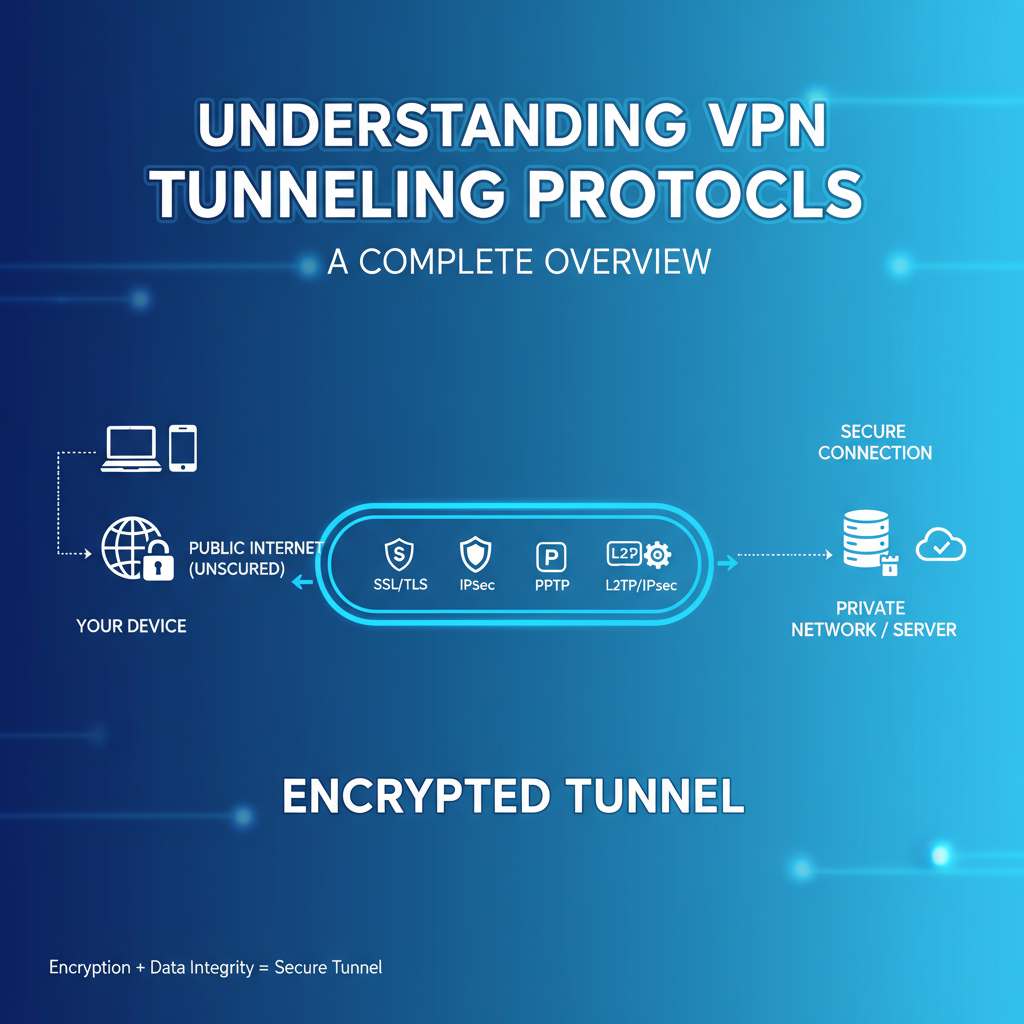
In today’s digital landscape, protecting your online privacy is more crucial than ever. One effective tool for accomplishing this is a VPN (Virtual Private Network) tunneling protocol. Understanding how it works can help you make informed decisions about your internet security.
VPN tunneling protocols create a secure “tunnel” between your device and the internet. This tunnel encrypts your data, preventing unauthorized access. By masking your IP address, it makes it difficult for anyone to track your online activities. Let’s dive deeper into the essentials of VPN tunneling protocols and their significance.
What is a VPN Tunneling Protocol?
A VPN tunneling protocol is a method used to send data securely over the internet. It establishes a protected point-to-point connection between your device and a VPN server. Essentially, this protocol ensures that only you and the intended recipient can access the data being transmitted. The primary goal is to keep your information safe from prying eyes.
How Does VPN Tunneling Work?
When you connect to a VPN, your internet traffic gets redirected through the VPN server. This process involves several key steps:
- Connection Initiation: After launching your VPN application, it builds a connection to a VPN server.
- Authentication: The server verifies your credentials, ensuring that unauthorized users cannot access the network.
- Tunneling: Once authenticated, data gets encapsulated within a secure tunnel, creating layers of encryption.
- Data Transmission: Your traffic is then routed through the VPN server, masking your IP address.
- Decryption: When data reaches its destination, it is decrypted and sent to your intended target.
Different Types of VPN Tunneling Protocols
There are several types of VPN tunneling protocols, each with its strengths and weaknesses. Here’s a look at some of the most popular ones:
- PPTP (Point-to-Point Tunneling Protocol): Known for its speed, PPTP is one of the oldest protocols but lacks robust security features.
- L2TP/IPsec (Layer 2 Tunneling Protocol): This protocol combines L2TP with IPsec for better security but can be slower due to double encapsulation.
- OpenVPN: An open-source solution that offers strong encryption and is highly configurable, making it a favorite among many users.
- SSTP (Secure Socket Tunneling Protocol): Developed by Microsoft, SSTP uses SSL for encryption, allowing it to bypass firewalls and proxy servers effectively.
- IKEv2/IPsec (Internet Key Exchange version 2): Provides fast reconnection speeds and is particularly effective for mobile devices.
Benefits of Using a VPN Tunneling Protocol
By using a VPN tunneling protocol, you unlock several advantages:
- Enhanced Security: Encryption protects your data from hackers and potential breaches.
- Privacy Protection: You can browse anonymously, keeping your online activities hidden.
- Geo-Restriction Bypass: Access content restricted in your region by connecting to a VPN server in another country.
- Safe Public Wi-Fi: Public networks are often insecure; using a VPN protects your data when connected to them.
- Improved Performance: Some VPNs can help reduce bandwidth throttling imposed by your internet service provider.
Choosing the Right VPN Tunneling Protocol
When selecting a VPN tunneling protocol, consider your specific needs:
- If speed is your primary concern, PPTP or IKEv2/IPsec might suit you.
- If security is your main focus, consider OpenVPN or SSTP for robust protection.
- For general use, L2TP/IPsec is a balanced choice between security and reliability.
Understanding VPN tunneling protocols is essential for safeguarding your online privacy. As cyber threats continue to evolve, employing the right VPN protocol can effectively protect your data from unauthorized access. Choose wisely based on your personal needs, and enjoy a safer online experience.
The Role of Encryption in VPN Tunneling
When using a Virtual Private Network (VPN), it’s crucial to understand how encryption plays a vital role in safeguarding your online experience. VPN tunneling creates a secure pathway for your data, but encryption is what ensures that the information traveling through this tunnel remains confidential and protected from prying eyes.
Encryption converts your data into a coded format that only authorized parties can read. When you send information over the internet without encryption, it travels through various networks and can be intercepted at any point. This makes sensitive data like passwords, credit card numbers, or personal messages vulnerable to theft. However, with encryption in VPN tunneling, your data is transformed into a format that is nearly impossible to decipher without the right key.
Here’s a closer look at how encryption works within VPN tunneling:
- Data Encoding: When you send data, the encryption process converts it into ciphertext. This scrambled format makes it unreadable to anyone who intercepts it.
- Preventing Unauthorized Access: Only the sender and intended receiver have the keys to decrypt and read the original information. This feature ensures that even if someone gains access to the data, they cannot understand it without the corresponding decryption key.
- Traffic Masking: Encryption hides not just the content of your data but also your internet activity. This means your online actions, like the websites you visit or files you download, are shielded from view.
Different types of encryption protocols exist, and each has its own strengths. Let’s explore a few common encryption protocols used in VPN tunneling:
- OpenVPN: This open-source protocol uses robust encryption methods such as AES-256. It is known for its high security and flexibility, making it a popular choice among users.
- IKEv2/IPsec: This protocol is swift and resilient, especially on mobile devices where connections might be inconsistent. It offers strong security features that keep your data safe.
- L2TP/IPsec: While L2TP on its own doesn’t encrypt data, when paired with IPsec, it provides a solid level of security suitable for many users.
- WireGuard: A newer protocol, WireGuard is praised for its efficiency and simplicity. It promises to deliver high security while also being fast.
The effectiveness of encryption hinges on the chosen protocol. Using a reliable tunneling protocol allows for better encryption, thus promoting a safer online environment. While some protocols are faster, their security may be compromised. It’s essential to find a balance that suits your needs—reliability in encryption without sacrificing speed.
Furthermore, the implementation of encryption is not just a technical detail; it’s also a vital part of privacy and security regulations around the globe. Data protection laws are becoming stricter, pushing more companies and individuals to prioritize encrypted VPN tunnels. With the rise in cyberattacks and privacy breaches, having a secure VPN that employs strong encryption can significantly minimize your risk.
Additionally, when using a VPN for sensitive tasks, be mindful of the encryption strength. Not all VPNs are created equal, and some might not use the strongest encryption available. Always choose reputable VPN services that clearly state their encryption protocols. Ensure they use modern encryption standards, as older methods may no longer provide sufficient security.
Encryption is an integral component of VPN tunneling that safeguards your data as it travels across the internet. By transforming your information into an unreadable format, it protects your personal data from interception. As you navigate the digital world, understanding the role of encryption in VPN technology is key to ensuring that your online activities remain private and secure. Ultimately, choosing the right VPN with strong encryption protocols helps enhance your digital safety and peace of mind.
Comparing Different Types of VPN Tunneling Protocols
When it comes to choosing a VPN (Virtual Private Network), one of the crucial aspects you’ll encounter is the different types of VPN tunneling protocols. Each of these protocols has unique features, benefits, and drawbacks, making them suitable for different use cases. Understanding these differences can help you decide which VPN protocol aligns with your needs for security, speed, and compatibility.
What Are VPN Tunneling Protocols?
VPN tunneling protocols create a secure connection between your device and a VPN server. They essentially “tunnel” your internet traffic through a secure pathway, protecting your data from potential threats. By using encryption, these protocols ensure that your personal information remains confidential while you browse the internet.
PPTP (Point-to-Point Tunneling Protocol)
PPTP is one of the oldest VPN protocols. It offers a good balance of speed and security but lacks the advanced encryption of newer protocols. Here are some key points about PPTP:
- Speed: Often faster than newer protocols.
- Security: Basic encryption methods, less secure than others.
- Compatibility: Works on most devices.
PPTP is ideal for users who prioritize speed and are less concerned about absolute security.
L2TP/IPsec (Layer 2 Tunneling Protocol with IPsec)
L2TP, combined with IPsec for added security, is a popular choice for many users. Although it may be slower than PPTP, it compensates with better encryption. Here are its notable features:
- Speed: Moderate speed, generally slower due to encryption.
- Security: Strong encryption, making it secure for sensitive data.
- Compatibility: Supported on various operating systems.
This protocol is great for those who need better security while still maintaining decent speed.
OpenVPN
OpenVPN has rapidly become one of the most preferred tunneling protocols. Its open-source nature allows for flexibility and high security. Check out these advantages:
- Speed: Highly efficient and can be optimized for better performance.
- Security: Uses robust encryption methods.
- Compatibility: Works on most devices and platforms, including routers.
OpenVPN is ideal for users who want a high level of security without sacrificing speed. It’s commonly used by businesses and tech-savvy individuals.
IKEv2/IPsec (Internet Key Exchange version 2)
IKEv2 is another strong contender, especially for mobile devices. It establishes a secure connection quickly and maintains it even when users switch networks. Here are some of its features:
- Speed: Fast reconnection after network changes.
- Security: Very secure with strong encryption.
- Compatibility: Best suited for mobile applications.
It is particularly beneficial for users who frequently switch between Wi-Fi and mobile data, offering excellent stability and speed.
SSTP (Secure Socket Tunneling Protocol)
SSTP was developed by Microsoft and is tightly integrated with Windows. This protocol uses SSL for encryption and can bypass many firewalls. Key points include:
- Speed: Generally good, though it may be affected by network conditions.
- Security: Offers high-level encryption.
- Compatibility: Primarily works with Windows devices.
SSTP is a solid option for Windows users looking for secure tunneling, especially in restrictive networks.
With various VPN tunneling protocols available, it’s essential to understand their differences. Whether you want speed, security, or compatibility, selecting the right protocol can enhance your online experience. Evaluate your needs and consider each protocol’s strengths to make an informed decision that aligns with your internet usage habits.
How VPN Tunneling Protocols Enhance Online Privacy
In today’s digital world, protecting your online privacy is more important than ever. One way to enhance your privacy is through VPN tunneling protocols. These protocols create a secure tunnel between your device and the internet, shielding your data from prying eyes. Here’s a closer look at how they function and why they matter.
Understanding VPN Tunneling Protocols
VPN tunneling protocols are crucial for ensuring your online activities remain private. They manage how your data is transported over the internet. When you connect through a VPN, these protocols encrypt your data and prevent unauthorized access. Essentially, they make your information unreadable to anyone trying to intercept it.
Types of VPN Tunneling Protocols
There are several types of VPN tunneling protocols, each with its unique advantages:
- PPTP (Point-to-Point Tunneling Protocol): This is one of the oldest protocols. It’s fast and easy to set up but may not be the most secure option.
- L2TP/IPsec (Layer 2 Tunneling Protocol): This combines L2TP with the security of IPsec, providing better security than PPTP while still being relatively fast.
- OpenVPN: This is an open-source protocol known for its high level of security and flexibility, making it a favorite among privacy advocates.
- IKEv2/IPsec (Internet Key Exchange version 2): Known for its speed and ability to reconnect quickly when internet access is interrupted, IKEv2 is particularly good for mobile users.
- SSTP (Secure Socket Tunneling Protocol): Utilized mainly in Windows environments, SSTP provides secure tunneling over SSL, which is robust for preventing leaks.
How VPN Tunneling Protocols Work
When you activate a VPN, the tunneling protocol kicks in. It starts by creating a secure connection, ensuring that all data transferred is encrypted. Here’s how it typically works:
- You connect to a VPN server through the chosen protocol.
- The protocol encrypts your data, which converts it into a secure form that makes it unreadable to anyone who might intercept it.
- Your data is sent through this secure tunnel to the VPN server.
- The VPN server decrypts the data and sends it to its destination.
- The returning data goes through the tunnel back to you, where it is re-encrypted again during the transfer.
Benefits of Using VPN Tunneling Protocols
Using a VPN tunneling protocol offers several key benefits for enhancing your online privacy:
- Increased Security: Encrypted data makes it exceptionally hard for third parties—like hackers or even your ISP—to read your activities.
- Anonymity: Your IP address is hidden, making it difficult for websites and advertisers to track your surfing habits.
- Bypassing Geo-Restrictions: Many people use VPN protocols to access content that may not be available in their region.
- Safer Public Wi-Fi: When using public Wi-Fi, hostile actors might try to intercept your data. A VPN protects you from these threats.
Considerations When Choosing a VPN Protocol
Not all VPN tunneling protocols are created equal. Here are important factors to consider before selecting:
- Speed: Choose a protocol that balances speed with security for a seamless experience.
- Security Features: Look for protocols that offer strong encryption and additional security features.
- Compatibility: Ensure the protocol works with your operating system and devices.
- User-Friendliness: Opt for protocols that are easy to set up and manage.
Choosing the right VPN tunneling protocol is crucial for maximizing your online privacy. By securing your internet connection, you not only safeguard your personal information but also enjoy a more private browsing experience. In a world where data is often misused, investing in a solid VPN tunneling protocol can be one of the smartest decisions you make for your online life.
Selecting the Right VPN Tunneling Protocol for Your Needs
When you’re looking to safeguard your online activities, choosing the right VPN tunneling protocol is essential. VPN tunneling protocols are the backbone of virtual private networks, controlling how your data travels from your device to the internet. Selecting the right one can enhance your security, speed, and overall browsing experience. Below are important factors to consider when selecting a tunneling protocol that fits your needs.
Understand Your Needs
First and foremost, identify what you intend to achieve with a VPN. Are you using it for streaming, secure browsing, or remote work? Your purpose will guide your choice of protocol:
- Streaming and Gaming: If you aim to access geo-restricted content or reduce lag while gaming, look for protocols prioritizing speed.
- Security: If your goal is to ensure extra security, select a protocol known for strong encryption and privacy features.
- Remote Access: For corporate purposes, a protocol allowing secure connections to your workplace network may be essential.
Popular VPN Tunneling Protocols
Familiarize yourself with the most commonly used VPN tunneling protocols. Each has its strengths and weaknesses:
- OpenVPN: This is widely regarded as one of the best options. It offers flexibility, security, and good speed. OpenVPN can work on various ports, which helps to bypass blocks placed by firewalls.
- IPSec: Often used in conjunction with other protocols, IPSec provides strong encryption and is great for securing internet traffic. It’s commonly used for remote work.
- L2TP/IPSec: Combining Layer 2 Tunneling Protocol (L2TP) with IPSec offers decent security, but it may be slower in performance compared to OpenVPN.
- PPTP: While it’s one of the oldest protocols, PPTP offers high-speed connections but lacks strong security features. It may not be suitable for users needing robust privacy.
- WireGuard: A newer protocol, WireGuard is gaining popularity for its simplicity and speed. It uses state-of-the-art cryptography and is very efficient.
Security Features
When choosing a VPN tunneling protocol, consider the security features it provides. The level of encryption is critical:
- Look for protocols offering at least 256-bit encryption for the highest standard of security.
- Ensure that the protocol supports advanced features like Perfect Forward Secrecy, providing additional protection for your data.
Speed and Performance
The speed of your connection can be affected by the protocol you choose. Each one has different impacts on latency and throughput:
- OpenVPN and WireGuard are usually faster than older protocols like PPTP, while maintaining a high-security standard.
- Your internet service can also impact speed; therefore, testing different protocols with your VPN service is advisable.
Device Compatibility
Make sure the protocol you select is compatible with all your devices. You want a solution that works seamlessly on:
- Computers (Windows, Mac)
- Smartphones (iOS, Android)
- Routers and Smart TVs
User-Friendly Experience
Consider how user-friendly the protocol is. Some protocols require technical knowledge to configure, while others come with straightforward apps:
- If you’re not tech-savvy, choose a provider that simplifies setup procedures and offers customer support.
- Documentation and tutorials can also significantly ease your experience.
Selecting the right VPN tunneling protocol involves understanding your specific needs and balancing between security and performance. By knowing what matters most to you—be it privacy, speed, or ease of use—you can make a well-informed choice that enhances your online activities effectively. Explore various protocols and take the time to experiment until you find the one that aligns perfectly with your requirements.
Conclusion
Understanding VPN tunneling protocols is crucial for anyone looking to enhance their online security and privacy. These protocols serve as the backbone of virtual private networks, enabling a secure connection between your device and the internet. By utilizing encryption, VPN tunneling ensures that your data remains confidential, safeguarding you against potential cyber threats and unauthorized access.
As you explored the various types of VPN tunneling protocols, it became clear that each has its unique advantages and features. From the versatile OpenVPN to the speedy PPTP, knowing the differences allows you to make an informed choice based on your specific needs. Whether you prioritize speed, security, or compatibility, understanding these functions is key to optimizing your online experience.
Furthermore, the enhanced privacy offered by VPN tunneling protocols cannot be overstated. They create a secure tunnel for your internet traffic, effectively masking your IP address and making it difficult for anyone to track your online activities. This added layer of anonymity is vital in today’s digital landscape, where privacy concerns are more pronounced than ever.
When selecting the right VPN tunneling protocol, consider factors like the level of security you require, the types of devices you use, and the activities you wish to perform online. Taking the time to assess your needs will ensure you choose a protocol that aligns with your online habits.
With the right VPN tunneling protocol in place, you can enjoy a safer and more private online experience. By prioritizing your digital security, you empower yourself to navigate the internet with confidence, knowing your information is protected.