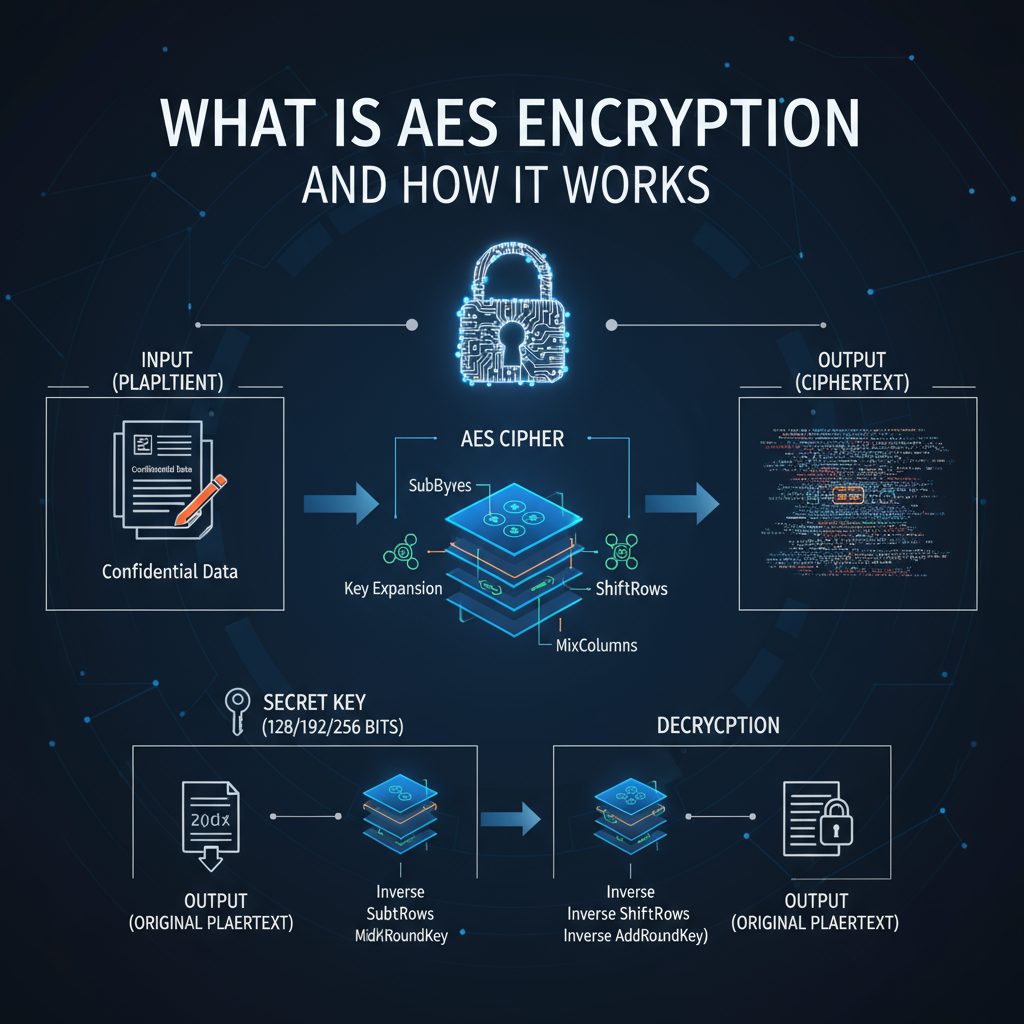
In today’s digital age, protecting sensitive information is more crucial than ever. One of the most effective methods to ensure data security is through AES encryption, a widely-used encryption standard. Understanding AES encryption can help you appreciate its significance in today’s technology-driven world.
What Is AES Encryption?
AES, which stands for Advanced Encryption Standard, is a symmetric encryption algorithm established by the National Institute of Standards and Technology (NIST) in 2001. It operates by using the same key for both encryption and decryption processes, making it essential to keep this key secure. AES encryption is known for its speed and effectiveness, making it ideal for a wide range of applications.
How AES Encryption Works
The working of AES encryption involves multiple steps, utilizing different rounds of transformations. Here’s a simplified breakdown of the process:
- Key Size: AES supports key sizes of 128, 192, and 256 bits. The length of the key affects the security level, with longer keys providing stronger protection.
- Block Size: AES encrypts data in blocks of 128 bits. If your data exceeds this size, it will be divided into multiple blocks.
- Rounds: The number of transformations applied to the data during encryption is referred to as rounds. AES uses 10 rounds for 128-bit keys, 12 for 192-bit keys, and 14 for 256-bit keys. Each round consists of four distinct steps.
These steps are:
- SubBytes: Each byte in the data block is substituted with another byte based on a predefined substitution table.
- ShiftRows: The rows of the data block are shifted cyclically to the left, enhancing diffusion.
- MixColumns: This step mixes the data in each column, ensuring that a small change in the input results in a significantly different output.
- AddRoundKey: The round key, derived from the initial key, is XORed with the data block to increase security.
After completing the specified number of rounds, the final output is the encrypted data. To decrypt, the same process is followed in reverse, using the same key. This simplicity is one of the reasons AES is favored worldwide.
Importance of AES Encryption
AES encryption plays a vital role in securing communications and protecting sensitive data. Its importance can be outlined as follows:
- Data Security: Whether it’s personal information, financial details, or confidential business data, AES encryption helps keep it secure from unauthorized access.
- Speed and Efficiency: Unlike other encryption methods that may slow down processes, AES is designed to work quickly without compromising security.
- Compliance: Many industries require the use of strong encryption methods to comply with regulations. AES meets and exceeds these standards, ensuring businesses adhere to necessary laws.
- Wide Application: From securing electronic transactions to encrypting files and data storage, AES is versatile and widely utilized across various platforms.
- Global Trust: AES is trusted and used by governments and organizations worldwide, which adds to its credibility as a robust encryption method.
Real-World Applications of AES Encryption
Understanding the practical applications of AES encryption can give you insights into its relevance in daily technology interactions. Here are a few notable instances:
- Banking Transactions: Online banking platforms use AES to protect customer information and transactions from cyber threats.
- VPN Services: Virtual Private Networks (VPNs) employ AES encryption to secure users’ internet connections.
- Messaging Apps: Many secure messaging applications utilize AES to keep conversations private and prevent data breaches.
Grasping the basics of AES encryption and its importance is vital for anyone navigating today’s digital landscape. Not only does it provide a layer of security for your data, but it also enhances trust in the technologies we rely on.
The Mechanism of AES Encryption: How It Secures Data
AES encryption is a widely used method that protects your sensitive data from prying eyes. It stands for Advanced Encryption Standard and has become the go-to choice for many organizations looking to secure their information. Understanding AES encryption is vital for anyone who wants to grasp how data protection works in our digital world.
Understanding the Basics of AES Encryption
AES operates on symmetric key encryption, which means that the same key is used for both encrypting and decrypting the data. The key length can vary—128, 192, or 256 bits. The longer the key, the harder it is for unauthorized users to crack the encryption. This flexibility allows organizations to choose a level of security that fits their needs.
How AES Works
The mechanism of AES encryption involves several steps that make it incredibly secure:
- Key Expansion: The original key is expanded into an array of key schedule words that are used in the encryption rounds.
- Initial Round: The first round includes an AddRoundKey step where the initial data block is combined with the first key from the key schedule.
- Rounds: AES has a series of 10, 12, or 14 rounds (depending on the key size). Each round includes:
- SubBytes: Each byte of the data block is replaced with a corresponding byte from a fixed table known as the S-box.
- ShiftRows: Rows of the data block are shifted cyclically to the left.
- MixColumns: The columns are mixed to provide further diffusion of the data.
- AddRoundKey: The result is combined with the next key from the key schedule.
- Final Round: The final round is similar to the previous rounds, except it does not include the MixColumns step.
Security Features
AES maintains high security through several mechanisms:
- Diffusion: This ensures that changing a single bit of plaintext results in a significant change in the ciphertext.
- Confusion: This concept obscures the relationship between the key and the ciphertext.
- Resistance to Attacks: AES has been rigorously tested against various attack methods, including brute force attacks.
Applications of AES Encryption
Many organizations utilize AES encryption to secure sensitive data. Here are a few common applications:
- Data Protection: Companies encrypt their databases to protect customer information.
- Secure Communications: AES is commonly used in securing email and messaging services.
- File Encryption: Individuals and businesses can encrypt files and folders to keep unauthorized users out.
- VPNs: Many Virtual Private Networks use AES to secure data transmitted over the internet.
The Importance of Using AES Encryption
In today’s digital age, protecting sensitive data is crucial. With increasing cyber threats and data breaches, using AES encryption provides peace of mind. It ensures that even if data is intercepted, it remains unreadable without the correct key.
As you engage with various online services, remember that AES encryption is often working in the background, shielding your sensitive information from potential threats. Embracing this technology not only fortifies your data security but also fosters trust among those you interact with online.
Understanding what AES encryption is and how it operates can empower you to make more informed decisions about your data security. Whether you are an individual or part of an organization, recognizing the importance of AES will guide you in protecting what matters most.
Different Modes of AES Encryption and Their Applications
AES, or Advanced Encryption Standard, is one of the most widely used encryption methods today. It plays a crucial role in securing data across various applications. However, while many are familiar with AES as a secure encryption standard, fewer are aware of the different modes of AES encryption and how they impact data security.
When we talk about modes of AES encryption, we’re referring to the different ways that the AES algorithm processes data. Each mode has distinct features, uses, and applications, which can affect both the security level and performance of encrypted data. Understanding these modes is essential for choosing the right one for your specific requirements.
Electronic Codebook (ECB) Mode
Electronic Codebook (ECB) mode is perhaps the simplest of all AES modes. In ECB mode, the data is divided into blocks, and each block is encrypted separately. This means that identical plaintext blocks will produce identical ciphertext blocks. Although ECB is straightforward, it has significant drawbacks. Since it doesn’t provide any form of randomization, it’s vulnerable to pattern analysis. Therefore, ECB is best avoided for sensitive information.
Cipher Block Chaining (CBC) Mode
CBC mode offers enhanced security over ECB. In this mode, each plaintext block is XORed with the previous ciphertext block before it is encrypted. This creates a dependence between blocks, meaning that identical plaintext blocks will yield different ciphertext blocks based on their position. CBC mode requires an initialization vector (IV) that is unique and unpredictable, making it much more secure than ECB. It’s commonly used in applications like secure file storage and network communications.
Counter (CTR) Mode
Counter mode (CTR) transforms the block cipher into a stream cipher. In this mode, a counter value is encrypted and then XORed with the plaintext to produce ciphertext. A notable advantage of CTR mode is its ability to allow simultaneous encryption and decryption, making it particularly fast and efficient. This makes CTR ideal for applications where speed is critical, such as in secure communications and real-time data protection.
Galois/Counter Mode (GCM)
Galois/Counter Mode (GCM) combines the features of CTR mode with authentication. It not only encrypts data but also provides integrity verification through an authentication tag. This means that any alterations to the ciphertext will be detected during decryption. GCM is widely used in secure communications over the internet, particularly in protocols such as TLS. Its ability to handle both encryption and authentication makes it suitable for modern applications that require high levels of security.
Cipher Feedback (CFB) Mode
CFB mode is designed to enable the encryption of data streams that come in variable lengths. It converts a block cipher into a self-synchronizing stream cipher. In CFB mode, the encryption of the previous ciphertext block is used to encrypt the next block of plaintext. CFB maintains error propagation; if one bit is altered, it will affect the next few decrypted bits. As a result, it’s suitable for applications such as encrypting network protocols where data may arrive in bits rather than fixed-length blocks.
Applications of AES Modes
Different encryption modes are suitable for different applications:
- Data at Rest: CBC and GCM are commonly used to encrypt stored data, such as files on a hard drive.
- Data in Transit: CTR and GCM modes are preferred for securing data during transmission to ensure fast and effective encryption.
- Streaming Data: CFB is useful for applications that handle data in a stream, such as video conferences or live communications.
Choosing the right AES mode depends on the specific needs and threat model of your application. Understanding the strengths and weaknesses of each mode is vital for ensuring your data remains secure. By selecting the appropriate mode, you can significantly enhance the security profile of any system reliant on AES encryption.
AES vs. Other Encryption Standards: A Comparative Analysis
When it comes to data security, encryption plays a crucial role in protecting sensitive information. Among the various encryption standards available, Advanced Encryption Standard (AES) stands out as one of the most widely adopted. However, understanding its performance in comparison to other encryption methods can help you make informed decisions for your security needs.
AES is a symmetric encryption algorithm that is highly regarded for its efficiency and effectiveness. It uses the same key for both encryption and decryption, which means that the key must remain secure. Other common encryption standards include RSA, DES, and Triple DES, each with its own unique features and use cases.
AES Characteristics
One of the defining features of AES is its use of block cipher encryption. AES operates on fixed-size blocks of data, typically 128 bits, and supports key sizes of 128, 192, or 256 bits. This flexibility allows organizations to balance security and performance based on their needs:
- 128-bit AES: Provides a high level of security and is efficient for many applications.
- 192-bit AES: Offers an increased level of security for sensitive data.
- 256-bit AES: Delivers the highest level of security, making it ideal for highly sensitive information.
Performance Comparison
When comparing AES to other encryption standards like RSA and DES, several factors should be considered, such as speed, security level, and resource consumption.
Speed
AES is generally faster than RSA because it is a block cipher that uses symmetric keys. This means it can encrypt and decrypt data more swiftly, making it suitable for real-time applications like video conferencing and online transactions. RSA, on the other hand, is an asymmetric algorithm known for being slower due to its complex mathematical operations. DES (Data Encryption Standard) and Triple DES, while historically popular, are no longer deemed secure enough for modern use cases and are considerably slower in performance compared to AES.
Security Level
Security is paramount in selecting an encryption standard. AES is routinely reviewed and strengthened to mitigate potential vulnerabilities. The National Institute of Standards and Technology (NIST) officially adopted AES in 2001, and it has since become a standard for protecting classified information in the U.S. Additionally, AES provides robust cryptographic strength against brute-force attacks, particularly with key sizes of 192 and 256 bits. Conversely, DES is now considered insecure due to its small key size of 56 bits, which can be easily cracked. While Triple DES improves upon DES by applying the algorithm three times, its efficiency and security are still inferior to AES.
Resource Consumption
When considering encryption methods, resource consumption matters. AES is optimized for performance, which means it can be efficiently executed even on devices with limited processing power. In contrast, RSA requires more resources because its key size (often 2048 bits or more for effective security) demands more processing capability. This makes AES a preferred choice for mobile devices and applications where battery life and performance are critical factors.
Use Cases
The choice of encryption standard often depends on specific use cases and requirements. AES is widely implemented across various sectors:
- Secure Communications: Utilized in VPNs and secure messaging platforms.
- Data Protection: Applied in securing file storage and backups.
- Financial Transactions: Used in online banking and payment processing systems.
In contrast, RSA is often used for secure key exchange in protocols like SSL/TLS, whereas DES and Triple DES are gradually being phased out in favor of AES due to their vulnerabilities.
AES consistently proves to be superior to many other encryption standards in terms of speed, security, and resource management. Depending on your specific needs, considering AES in your encryption strategy can enhance your data security and streamline your operations.
Practical Steps to Implement AES Encryption in Your Systems
AES (Advanced Encryption Standard) is a powerful algorithm used for securing sensitive data. Implementing AES encryption in your systems can significantly enhance data security and protect against unauthorized access. If you are looking to implement AES encryption, here are some practical steps to guide you along the way.
Understanding AES Encryption
AES is a symmetric key encryption method, meaning it uses the same key for both encryption and decryption. The key can be 128, 192, or 256 bits in length, with 256 bits being the most secure option. Understanding how AES operates is crucial before diving into the implementation process.
Steps to Implement AES Encryption
Follow these fundamental steps to successfully implement AES encryption in your systems:
- Determine Your Use Case:
- Identify the specific data that needs protection, such as personal information, financial records, or intellectual property.
- Assess the risk level associated with potential data breaches.
- Select the Appropriate Key Size:The strength of AES encryption is largely dependent on the key size you choose. A larger key size typically offers better security but may require more computing resources. For most applications, a 256-bit key is recommended for optimal security.
- Choose an AES Library:Select a reliable AES library that suits your programming language and platform. Popular options include:
- OpenSSL for C/C++
- PyCrypto for Python
- Java Cryptography Extension (JCE) for Java
- Bouncy Castle for several languages
- Generate a Secure Key:It’s essential to generate a secure key that is random and unique to your system. Use a strong random number generator to ensure that your key is not predictable. Store this key safely, as losing it means you cannot decrypt your data.
- Implement the Encryption Process:Once you have your library and key, it’s time to implement the encryption process. Follow these steps:
- Convert your plaintext data into bytes.
- Use the AES library to apply the encryption algorithm to these bytes with your chosen key.
- The output will be your encrypted data, known as ciphertext.
- Implement the Decryption Process:Decryption is the reverse of encryption. Use the same AES library and key to decrypt the ciphertext back into plaintext. Make sure to handle errors gracefully in case of incorrect keys or corrupted data.
- Test the Implementation:Thoroughly test your implementation to ensure it works as expected. Check both encryption and decryption. Validate that the decrypted data matches the original plaintext.
- Monitor and Update Security Policies:Regularly review your security practices and keep your AES library up to date. Vulnerabilities in libraries can be discovered over time, so maintaining updated software is key to ongoing security.
Common Pitfalls to Avoid
While implementing AES encryption can provide robust security, there are common pitfalls to be cautious of:
- Using weak keys or reuse of the same key over a long period.
- Neglecting to securely store the key and allowing it to be exposed.
- Failing to keep your encryption library updated.
Final Recommendations
Implementing AES encryption is a sound decision for safeguarding your sensitive data. Always keep user experience in mind while executing security protocols, ensuring that the encryption does not overly burden system performance. Stay informed about best practices in encryption to continually protect your systems against evolving threats.
By following these practical steps and recommendations, you can effectively implement AES encryption in your systems, enhancing data security, and providing peace of mind.
Conclusion
To wrap up our exploration of AES encryption, it’s clear that this technology plays a vital role in safeguarding sensitive information across various sectors. Understanding what AES encryption is and recognizing its importance lays the foundation for effective data protection strategies. By delving into how AES secures data, you can grasp the intricate mechanisms that make it robust against unauthorized access.
The different modes of AES encryption cater to diverse applications, ensuring flexibility based on specific security needs. Whether for encrypting files, network communications, or securing cloud data, these modes allow users to implement AES effectively in varying contexts. Additionally, comparing AES with other encryption standards highlights its superior security features, making it a preferred choice for businesses and individuals alike.
For those looking to implement AES encryption in their systems, practical steps are available to simplify the process. By leveraging tools and software designed for AES encryption, you can enhance data security without needing extensive technical expertise. Following best practices in implementation helps ensure that your sensitive information remains protected against threats.
Embracing AES encryption is not just about adopting a technology; it’s about establishing a culture of security. By prioritizing data protection through AES, you enable a safer digital environment, allowing you to operate with confidence, knowing your information is well-guarded. As cyber threats continue to evolve, staying informed and proactive about encryption methods like AES is crucial for anyone committed to data security.