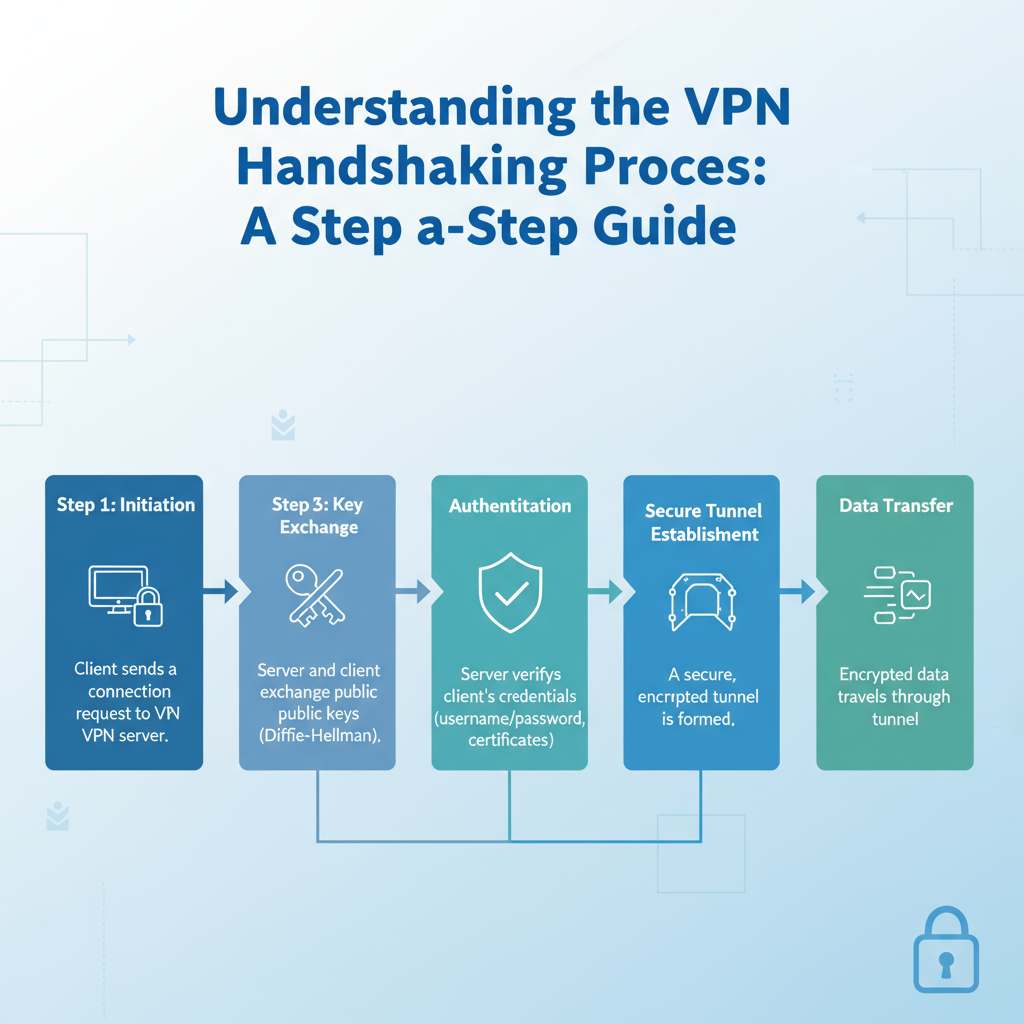
In the world of virtual private networks (VPNs), understanding the handshaking process is crucial for establishing secure connections. The VPN handshaking process allows two devices to authenticate each other and agree on how to communicate securely. Let’s explore this process step-by-step, making it easy to understand.
The VPN handshaking process involves several key steps. Here’s a breakdown:
Connection Initiation
The process begins when your device sends a connection request to the VPN server. This request includes crucial information, such as the version of the VPN protocol being used.
Authentication
Upon receiving the connection request, the VPN server verifies the client’s credentials. This step is essential to ensure that the user is authorized to access the VPN service. Common authentication methods include username and password combinations, digital certificates, or multi-factor authentication.
Pre-Master Secret Exchange
After successful authentication, both the client and server generate a pre-master secret. This secret is critical for creating session keys that encrypt your data. They use a secure key exchange algorithm—most commonly, the Diffie-Hellman key exchange—to generate this secret without directly transmitting it over internet.
Session Key Creation
Using the pre-master secret, both devices independently generate session keys. These session keys are used for encrypting the data exchanged for the duration of the VPN session. They ensure that any information transferred over the connection is secure and private.
Confirmation
Once the session keys are created, both the client and server send confirmation messages to each other. This ensures that both parties are ready to communicate securely. At this point, the handshaking process is nearly complete!
Secure Data Transmission
The VPN is established. Your device and the VPN server can now exchange data securely. All transferred data is encrypted using the session keys created earlier, protecting it from potential eavesdroppers.
This entire handshaking process usually happens in a matter of seconds or less, providing users with secure access to the internet or private networks. But why is understanding this process important for you?
First, knowing how the VPN handshaking process works can help you troubleshoot any connectivity issues. If you frequently have difficulty connecting to a VPN, understanding these steps may help you identify what might be going wrong. For instance, issues during the authentication phase could indicate a problem with your login credentials.
Second, being aware of how the handshaking process secures your data can enhance your trust in using VPNs. Knowing that your information is encrypted and that there are measures in place to authenticate your identity can offer peace of mind as you browse the web.
Understanding the handshaking process can empower you to make informed decisions when choosing a VPN service. Some VPNs may not employ robust handshaking protocols, leading to potential vulnerabilities. Selecting a VPN provider that uses strong encryption and authentication methods helps ensure your online safety.
The VPN handshaking process is a vital component in creating a safe and secure connection between your device and a VPN server. By following this structured approach, VPNs can protect your data from unauthorized access and provide a layer of anonymity as you navigate the online world.
Don’t overlook the importance of selecting a high-quality VPN provider. A reliable service will not only ensure secure handshakes but also optimize your browsing experience for speed and efficiency. As you explore your options, consider reading user reviews and researching the technology behind each VPN to ensure you find the right fit for your needs.
By gaining a solid understanding of the VPN handshaking process, you can better appreciate the security measures that safeguard your online activities while making informed choices about the tools you use.
The Importance of Encryption in VPN Handshakes
When you connect to a Virtual Private Network (VPN), one of the key components of a secure connection is the encryption that takes place during the handshake process. Understanding this significance goes a long way in ensuring your online safety and privacy. The handshake process sets the stage for the connection, allowing devices to establish trust and secure communication.
Encryption in VPN handshakes is crucial because it secures the data exchanged between your device and the VPN server. This security ensures that even if someone intercepts the data being transmitted, they cannot read or manipulate it. Without encryption, your personal information, online activities, and other sensitive data could potentially fall into the wrong hands. Here are several reasons why encryption is a top priority in the VPN handshake process:
Data Privacy
Encryption ensures that your data remains private. Only you and the intended recipient can read the information being shared. This level of security is especially important when using public Wi-Fi networks, where cybercriminals often lurk to capture personal data.
Data Integrity
With encryption, the integrity of the data is protected. If the data is altered in transit, encryption algorithms help detect such changes. This feature gives you peace of mind, knowing that the information you receive is exactly as it was sent.
Authentication
The handshake process uses encryption to authenticate both parties involved. It verifies that the device you are connecting to is indeed the VPN server and not an impostor. This authentication prevents man-in-the-middle attacks, where hackers could intercept and redirect your connection.
Limited Exposure
By utilizing strong encryption protocols during the handshake, VPNs limit the exposure of your data. If a hacker were to try and eavesdrop, the data they capture would be gibberish, offering them no useful information.
The process begins when you initiate a connection to a VPN server. Your device sends a connection request, which sets off the handshake. During this phase, cryptographic keys are exchanged, further strengthening the security of your session. Both sides use these keys to encrypt the data that flows between them. Thus, encryption is not just an added layer of security; it’s fundamental to the entire handshake process.
Various encryption protocols can be employed during a VPN handshake, each with its strengths. For example:
OpenVPN
This is one of the most popular protocols known for its high security and flexibility. It uses OpenSSL for encryption, making it robust against many types of attacks.
IPSec
Often used in tandem with other protocols, IPSec offers strong encryption and is widely adopted across different devices and operating systems.
L2TP
This is a tunneling protocol that, when combined with IPSec, provides a dual layer of encryption. It’s advantageous for ensuring secure communication.
It’s essential to choose a VPN that employs strong encryption standards. The key factor is to ensure the encryption methods used are up-to-date, as outdated encryption can become vulnerable to cyber threats. Maintaining robust encryption during the handshake process can help safeguard your data against evolving security risks.
In addition to choosing the right encryption protocols, it’s essential to keep your VPN software current. Developers constantly improve software to patch vulnerabilities and enhance security. Regular updates ensure that you benefit from the latest advancements in encryption techniques.
When engaging in online activities, you might not always consider the intricacies of what happens beneath the surface. Still, the importance of encryption in ensuring that your VPN handshake is secure cannot be overstated. By utilizing effective encryption methods, you fortify your online presence, enhance your data privacy, and protect yourself from potential online threats.
Recognizing the role of encryption in VPN handshakes is critical to understanding how your data remains protected in transit. By selecting VPN solutions that prioritize strong encryption techniques, you not only improve your online security but also foster greater transparency and trust in your digital communications.
Common Issues During the VPN Handshaking Process and How to Solve Them
During the VPN handshaking process, several common issues can arise, potentially interrupting your secure connection. Understanding these problems and knowing how to troubleshoot them can enhance your overall VPN experience. Below are the prevalent issues users encounter during the VPN handshaking process and practical solutions to resolve them.
Connection Timeouts
One of the most frequent issues during the VPN handshaking process is connection timeouts. This often happens when the VPN client cannot communicate with the server effectively, causing the handshake to fail.
Solution: To fix connection timeouts, first, check your internet connection. Try resetting your modem and router. Next, ensure that your VPN server is reachable. You can do this by trying to connect to a different server within the VPN provider’s network. If the issue persists, consider adjusting your VPN settings, such as changing the protocol used for the connection.
Firewall and Antivirus Interference
Firewalls and antivirus software can sometimes block VPN traffic, halting the handshaking process. This can create frustration for users trying to establish a secure connection.
Solution: To avoid this issue, you can temporarily disable your firewall or antivirus software to see if it resolves the handshaking problem. If successful, you may need to configure your security software to allow VPN traffic. Look for options to add exceptions for your VPN application in the settings of your firewall or antivirus software.
Incorrect Login Credentials
Providing incorrect login credentials can lead to handshake failures. If the authentication fails, the handshake process cannot continue, resulting in connection issues.
Solution: Double-check your username and password to ensure they are entered correctly. If you have forgotten your credentials, use the password recovery option provided by your VPN service. Keep in mind that some VPNs may require two-factor authentication, so make sure to follow all security steps.
Protocol Compatibility
The choice of VPN protocol can also affect the handshaking process. Some devices or networks may not support certain protocols, leading to failed connections.
Solution: Adjust the VPN protocol in your settings. Most VPN providers offer various protocols such as OpenVPN, IKEv2, and L2TP. Testing different protocols can help identify compatibility issues. For mobile devices, IKEv2 is often recommended for its speed and stability.
Network Configuration Issues
Problems with your local network configuration, such as incorrect DNS settings or IP address conflicts, can significantly affect your VPN handshake process.
Solution: Ensure that your DNS settings are correctly configured. You might want to switch to Google’s DNS (8.8.8.8 and 8.8.4.4) or Cloudflare’s DNS (1.1.1.1) for better compatibility. Additionally, make sure that there are no IP address conflicts on your network, as this can prevent successful communication with the VPN server.
Data Plan Limitations
If you’re using a limited mobile data plan, you might run into problems during the VPN handshaking process. Excessive data use can trigger restrictions from your ISP.
Solution: Monitor your data usage closely. If you’re nearing your limit, consider switching to Wi-Fi to complete the VPN connection. Alternatively, most VPN clients allow you to set a data limit within the app, which could prevent interruptions.
Server Overload
Sometimes, the VPN server you are trying to connect to is overloaded with too many users. This can lead to delayed responses during the handshaking process.
Solution: If you suspect server overload, switch to a less crowded server. Most VPN services offer quick access to different server locations. Try connecting to a server that is geographically closer to you or one that is recommended for performance.
VPN Leaks
Another common issue that can compromise your security during the VPN handshaking process is VPN leaks, where your real IP address or DNS requests are exposed despite being connected to a VPN.
Solution: To prevent VPN leaks, ensure your VPN service has proper leak protection features. You can learn more about how to prevent VPN leaks and DNS leaks to maintain your privacy and security.
Knowing these common issues and their solutions can save you time and reduce frustration when encountering problems during the VPN handshaking process. By being proactive and understanding these potential pitfalls, you can ensure a smoother, more secure connection every time you connect to your VPN.
Comparing Different VPN Protocols and Their Handshaking Mechanisms
When you connect to a VPN (Virtual Private Network), you might wonder how your device keeps its connection secure. One key aspect of this security is the handshake process, which establishes how your device and the VPN server communicate. Different VPN protocols handle this handshaking differently, affecting speed, security, and overall performance. Let’s explore how various VPN protocols operate, focusing on their specific handshaking mechanisms.
OpenVPN
OpenVPN is one of the most popular VPN protocols due to its flexibility and strong security. The handshaking process in OpenVPN relies on SSL/TLS for key exchange, ensuring that your data remains private. During the handshake, OpenVPN employs a two-step verification method. First, it authenticates the server to confirm it’s the right one you’re connecting to. Then, it sends and receives cryptographic keys through a secure channel. This method requires additional CPU resources but provides a high level of security.
L2TP/IPSec
L2TP (Layer 2 Tunneling Protocol) paired with IPSec (Internet Protocol Security) is another common protocol. This combination uses a two-phase handshaking process. In the first phase, L2TP sets up a tunnel, while IPSec provides encryption. The handshake process involves a mutual authentication step, where both the client and server present their credentials. This approach enhances security but may introduce latency, making it slower compared to OpenVPN.
PPTP
PPTP (Point-to-Point Tunneling Protocol) is an older but widely used protocol, mainly for its speed. The handshaking process in PPTP is relatively straightforward. It uses a simple 4-way handshake to establish the connection. This means that the client sends a request to the server, and the server replies with its credentials. Then they exchange a session key for encryption. While this process is fast, PPTP lacks the strong security features found in newer protocols, leaving it vulnerable to various attacks.
SSTP
Secure Socket Tunneling Protocol (SSTP) is another VPN option, particularly favored in Windows environments. SSTP uses SSL to secure its connections, similar to OpenVPN. The handshaking process involves establishing an SSL connection between the client and server. Once this is done, a secure tunnel is created for encrypted data transmission. This structure not only enhances security but also helps bypass firewalls more effectively, making it a practical choice for users in restrictive networks.
IKEv2/IPSec
Internet Key Exchange version 2 (IKEv2), combined with IPSec, is recognized for its speed and stability, especially on mobile devices. The handshake process here is efficient, featuring a 3-phase method. First, both parties authenticate each other. Second, they agree on encryption methods, followed by exchanging keys. IKEv2/IPSec’s seamless reconnection feature makes it ideal for those who frequently switch networks or move between Wi-Fi and cellular data.
WireGuard
WireGuard is a modern protocol that is gaining popularity for its simplicity and high performance. The handshaking process in WireGuard is designed to be quick and efficient. It uses a single round trip to negotiate keys, which reduces latency. With only 4 lines of code for the entire protocol, its compact structure allows for fast handshakes and robust security without the overhead of complex configurations. This efficiency is one reason why many are turning to WireGuard as a preferred VPN option.
Each VPN protocol employs a unique handshaking process that influences performance and security. OpenVPN and IKEv2/IPSec stand out for their strong security features, while PPTP is often chosen for speed despite its vulnerabilities. Understanding these differences can help you select the right protocol based on your needs, whether it’s for secure browsing, accessing restricted content, or maintaining online privacy.
When choosing a VPN, consider what matters most to you: speed, security, or compatibility. By knowing how these protocols handle the critical handshaking process, you can make a more informed decision when selecting a VPN service.
The Role of Certificates in Establishing VPN Connections
In the realm of online security, Virtual Private Networks (VPNs) play a major role in protecting data. One of the critical components of establishing secure VPN connections is the use of digital certificates. But what do these certificates do, and why are they essential for VPN functionality?
Digital certificates act as a digital form of identification. They are issued by trusted third parties known as Certificate Authorities (CAs). These certificates contain vital information, including the public key for encryption and the identity of the certificate holder. When you establish a VPN connection, these certificates verify both ends of the connection. This ensures that you are indeed connecting to a legitimate server and not an imposter.
How Digital Certificates Work in VPNs
When you initiate a VPN connection, a handshake process occurs between your device and the VPN server. During this process, the following steps take place:
Certificate Exchange
Your VPN client requests the server’s certificate. In return, the server sends its certificate to your client. This exchange is crucial to confirm the server’s identity.
Certificate Verification
After receiving the server’s certificate, your device checks its validity. It looks for specific details such as expiration date and whether the certificate is signed by a trusted CA. You can learn more about how to verify website security certificates to understand this process better.
Public Key Retrieval
Once verified, your VPN client extracts the server’s public key from the certificate. This key will be used to encrypt the data exchanged between your device and the server.
Session Key Generation
Your device creates a unique session key, which is then encrypted with the server’s public key. It sends this encrypted session key back to the server.
Secure Tunnel Establishment
With both sides having the session key, a secure tunnel is established. Any data transferred between your device and the server is now protected.
Benefits of Using Certificates
Utilizing digital certificates to establish VPN connections offers several benefits:
Authentication
Certificates provide a layer of trust. They help ensure the identity of the server, which means you can feel confident that you’re connected to the right source.
Encryption
Certificates enable the use of public and private key pairs. This creates a strong encryption system for your data, protecting it from prying eyes.
Data Integrity
By verifying certificates, VPNs ensure that the data remains unchanged during transit. This prevents potential tampering by malicious actors.
Non-repudiation
The use of certificates means that the server cannot deny having sent a message. This adds accountability, making it harder for fraud to take place.
Types of Certificates Used in VPNs
There are different types of certificates employed in VPN setups. Choosing the right one matters significantly for your security. Here are the most common types:
Server Certificates
Used to authenticate the VPN server to the client. Ensures the client is communicating with a legitimate server.
Client Certificates
Used to verify the identity of the client accessing the VPN server. This enhances security by ensuring that only authorized users can establish a connection.
Root Certificates
These are the trust anchors. They are what the client and server trust when verifying other certificates. This certificate must be installed on the device to establish trust.
The process of establishing a VPN connection can seem complex, but it boils down to effective verification and encryption. Using digital certificates acts as a foundational element in ensuring that your data is handled securely. By validating identities and safeguarding data integrity, these certificates make your online experience safer and more secure.
Digital certificates serve a crucial role in the establishment of VPN connections. They provide essential verification, encryption, and data integrity, making them indispensable in the world of online security. Understanding their importance can help you make informed decisions about your VPN choices and improve your overall safety while browsing the web.
Conclusion
Navigating the intricate nature of the VPN handshaking process is essential for anyone looking to harness the power of virtual private networks. As we’ve explored, understanding each step of this process not only enhances your knowledge but also empowers you to utilize VPNs more effectively. Encryption plays a pivotal role in the security of these connections, ensuring your data remains safe from prying eyes during the handshake.
Common issues can arise, but being aware of them allows you to troubleshoot effectively, ensuring a smoother and more secure VPN experience. Additionally, comparing different VPN protocols sheds light on their unique handshaking mechanisms, helping you choose the best fit for your needs.
Certificate management is another vital component, as these digital files establish trust between devices, playing a key role in securing your connection. By grasping these concepts, you can make informed decisions about your online security. This knowledge not only enhances your online privacy but also equips you to tackle any challenges that may surface during the VPN handshaking process.
Ultimately, a deeper understanding of how VPNs function can help you safeguard your digital presence in an increasingly connected world. To further enhance your knowledge, you might want to explore differences between remote access VPN and site-to-site VPN or learn more about what is cybersecurity to better understand the broader security landscape.