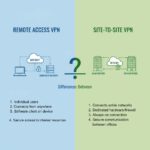
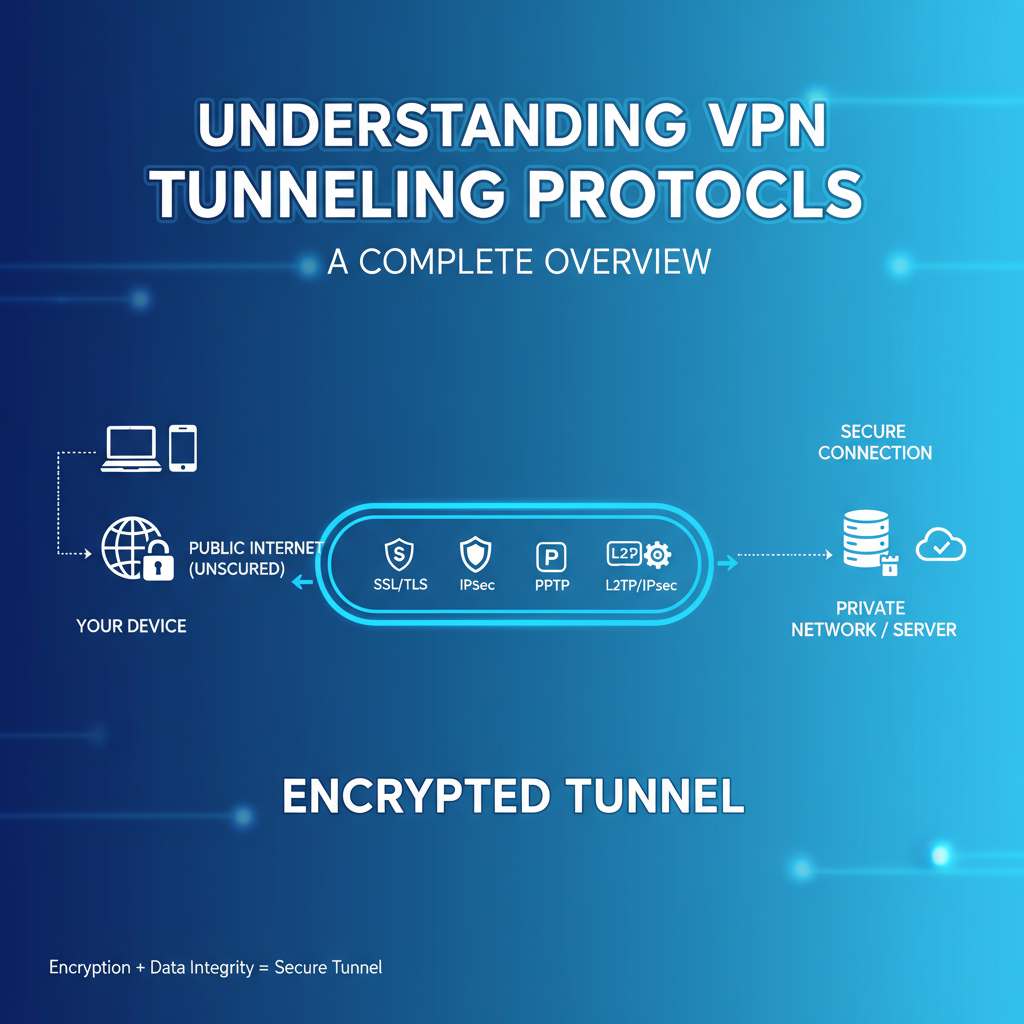
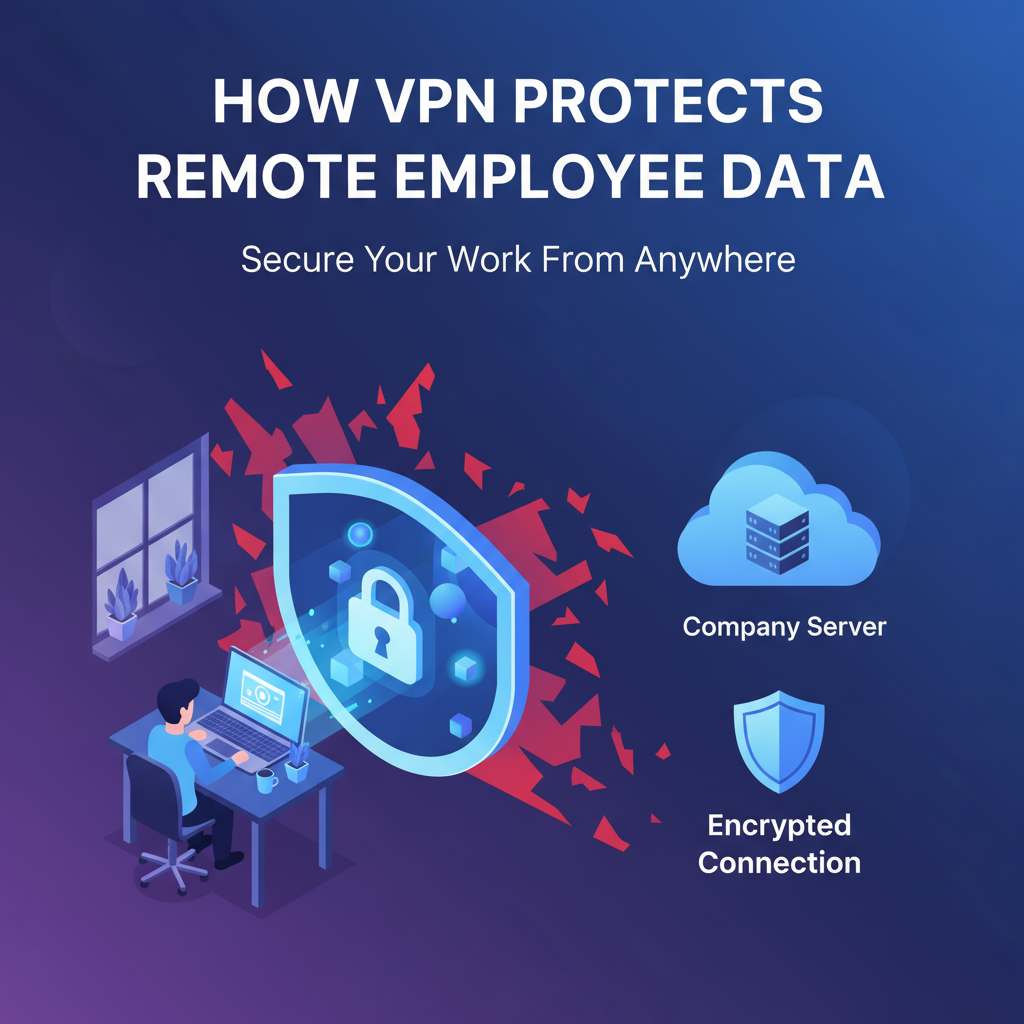
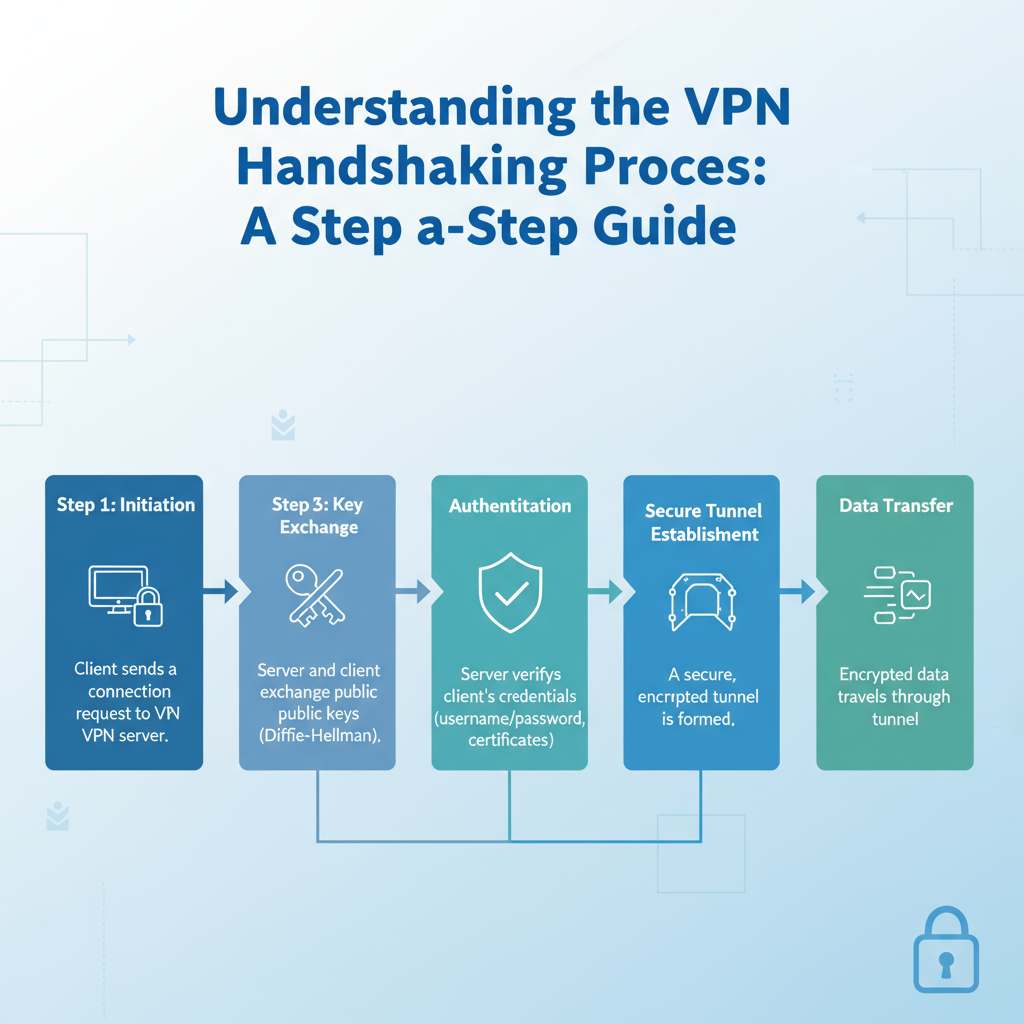
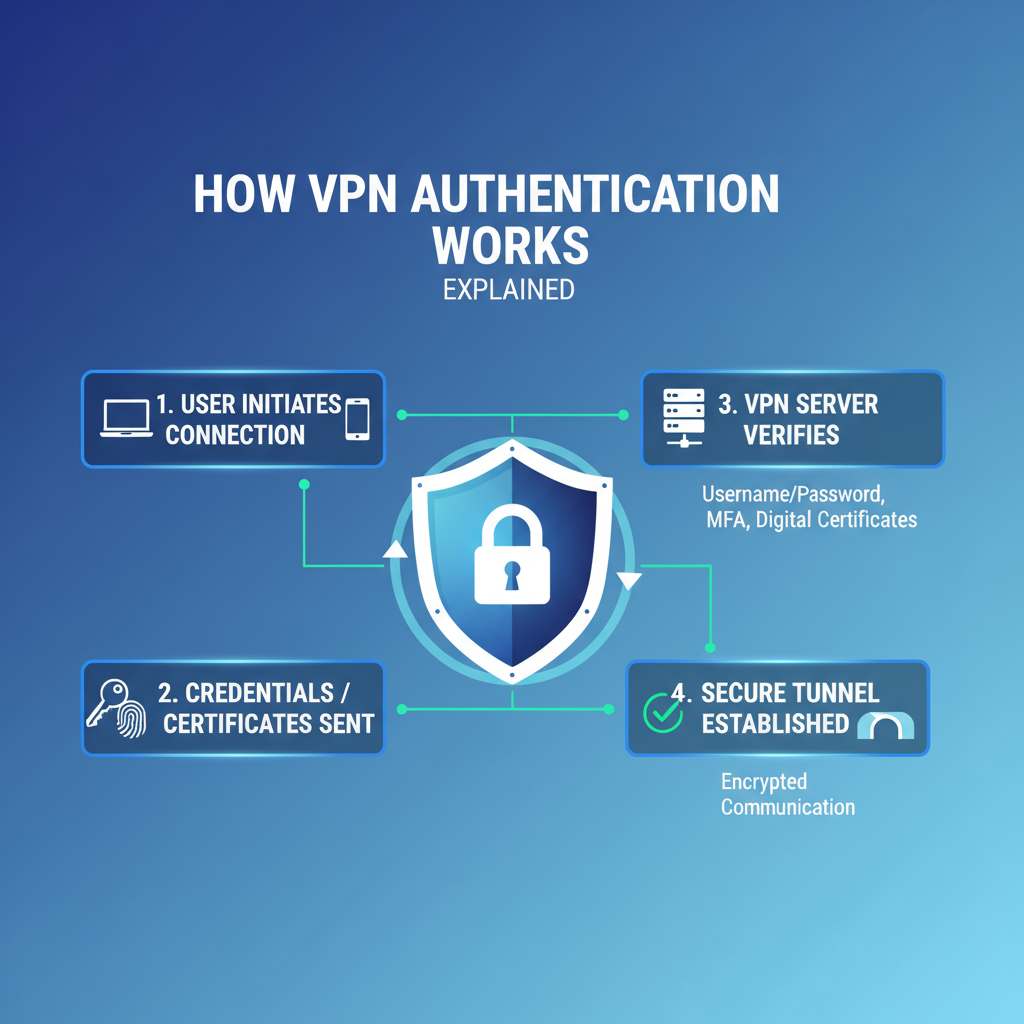
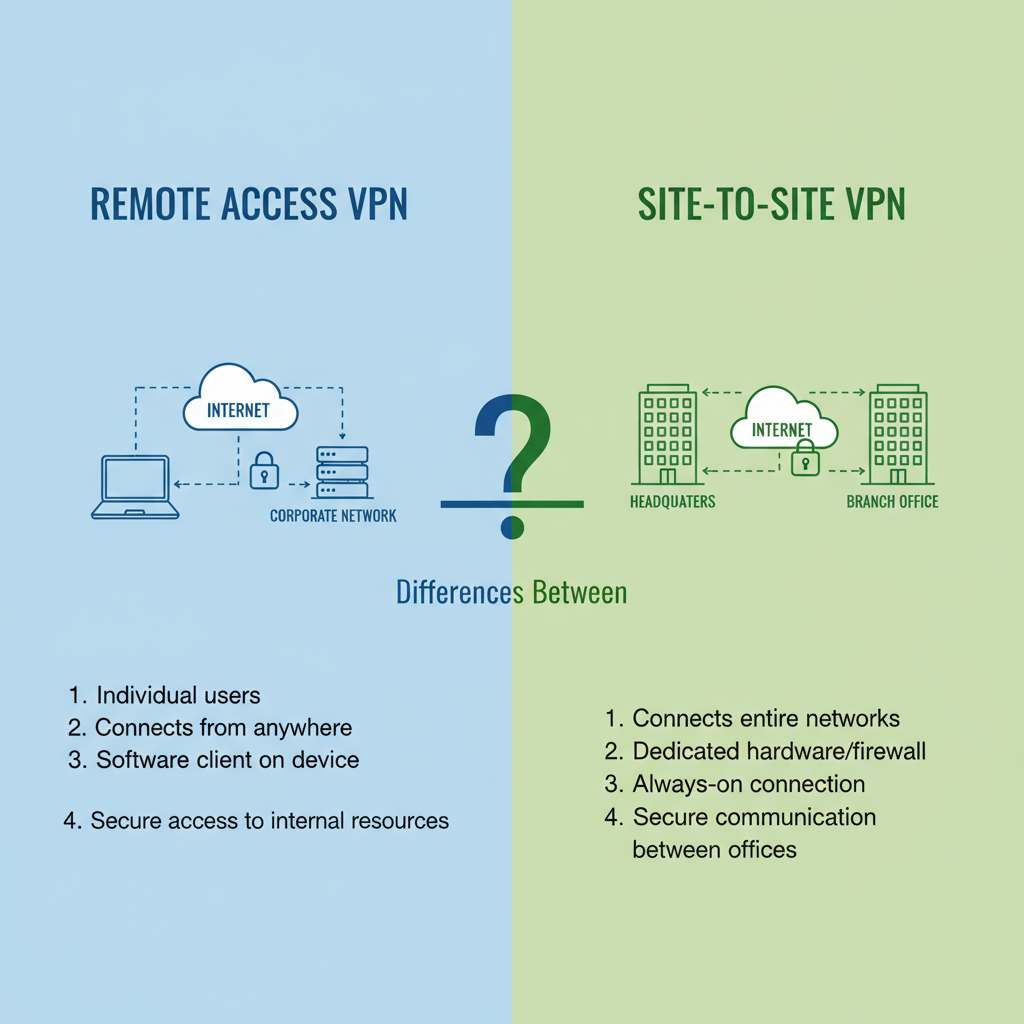
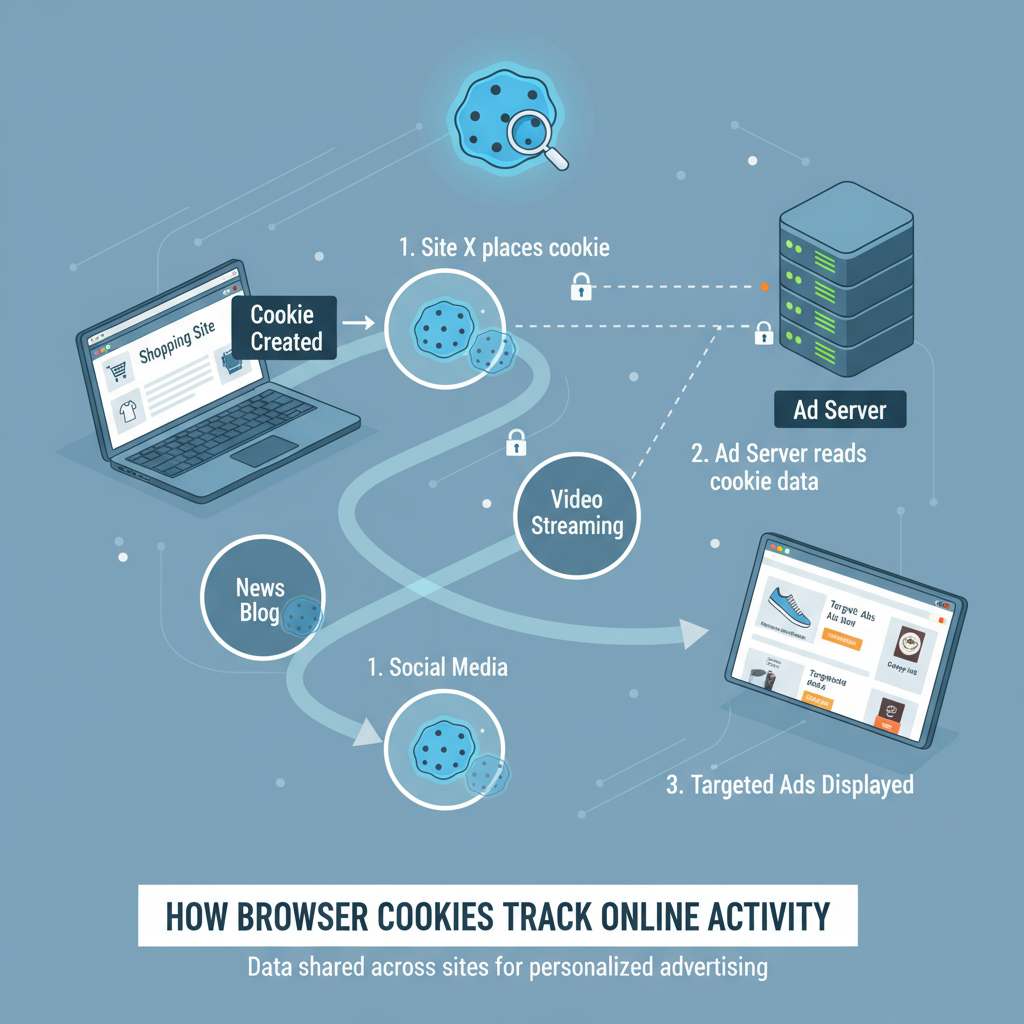
Understanding VPN Tunneling Protocol: A Complete Overview
In today's digital landscape, protecting your online privacy is more crucial than ever. One effective tool for accomplishing this is a VPN (Virtual Private Network) tunneling protocol. Understanding how it works can…